Choosing the right endpoint solutions is crucial for balancing productivity and security in today's dynamic digital landscape.
With the proliferation of remote work, BYOD (Bring Your Own Device) policies, and sophisticated cyber threats, organizations must adopt robust strategies to protect their endpoints without hindering user efficiency.
Understanding Endpoint Solutions
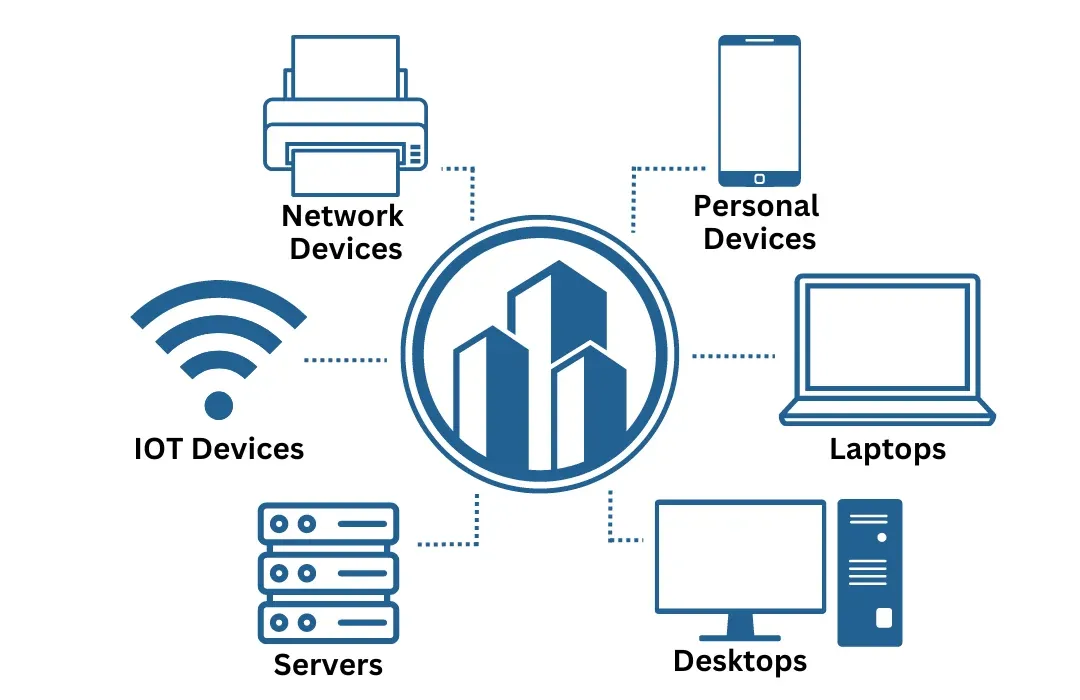
Endpoint solutions encompass tools and practices designed to secure and manage devices like laptops, smartphones, tablets, and desktops that connect to a corporate network.
These solutions aim to protect against threats such as malware, unauthorized access, and data breaches while ensuring seamless device performance.
Key Considerations for Selecting Endpoint Solutions
1. Security Capabilities
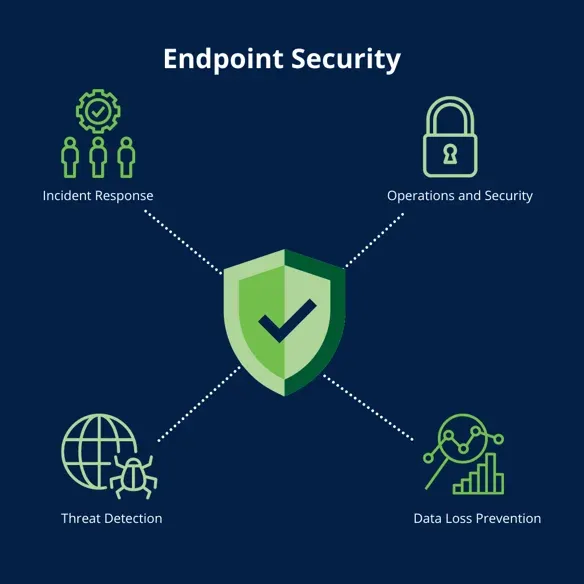
-
Comprehensive Threat Protection: Ensure the solution offers protection against a wide range of threats, including viruses, ransomware, phishing, and zero-day attacks.
-
Real-Time Monitoring: Look for solutions that provide continuous monitoring and immediate response to threats.
-
Advanced Detection Techniques: Utilize tools that employ behavioral analysis and machine learning to detect anomalies and potential threats.
2. Productivity Features
An ideal endpoint solution should operate with minimal performance impact, ensuring it doesn’t slow down devices or interrupt user workflows.
It must also feature a user-friendly interface that enables both IT administrators and end-users to navigate and use the tool with ease.
Additionally, support for remote management is essential—allowing IT teams to configure, monitor, and troubleshoot devices from anywhere, which is especially valuable in today’s distributed work environments.
3. Integration and Compatibility
A robust endpoint solution should offer cross-platform support to ensure compatibility with the diverse range of operating systems and devices used across the organization.
Equally important is seamless third-party integration, allowing the solution to work in harmony with existing security tools, SIEM systems, and broader IT infrastructure. This interoperability ensures streamlined operations and a more cohesive security ecosystem.
-
Adaptability: The solution should scale with the organization's growth and adapt to changing security needs.
-
Customization: Offers customizable policies and settings to align with specific organizational requirements.
4. Compliance and Reporting
An effective endpoint solution must support regulatory compliance by aligning with industry-specific standards such as GDPR, HIPAA, or PCI DSS.
This not only reduces legal and financial risks but also builds trust with stakeholders.
Additionally, the solution should offer detailed reporting capabilities, generating comprehensive logs and audit-ready reports to support security assessments and compliance audits.
Best Practices for Implementation
-
Conduct a Thorough Assessment: Evaluate the organization's specific needs, existing infrastructure, and potential risks.
-
Pilot Testing: Implement the solution in a controlled environment to assess its effectiveness and identify any issues.
-
Employee Training: Educate staff on security best practices and how to interact with the endpoint solution.
-
Regular Updates and Patching: Keep the solution and all endpoints updated to protect against known vulnerabilities.
-
Continuous Monitoring and Evaluation: Regularly review the solution's performance and make necessary adjustments.







